3 Ways to Level Up your IoT Security Right Now

The Importance of IoT Security

Having your personal desktop compromised is one thing. Leaking personal data from 1,000s of devices in your remote deployment due to poor IoT security? That’s something entirely different.
IoT security is a huge concern for many businesses. After all, much of the information being collected is sensitive data that has been entrusted to these companies by their clients. Jeopardizing their information could result in lost business, disgruntled customers and a tarnished reputation.
Don’t worry, we’ve got your back — here are 3 quick and easy ways to keep your data where it belongs: safe and sound within your network.
Invest in a Virtual Private Cloud
When information hits the public Internet, it can be vulnerable to external threats. One way to bypass this risk is by never exposing data to the threat. This can be done with AWS virtual private cloud (VPC) peering, which allows you to connect your IoT devices to resources within the safety of your virtual private cloud — all without using the Internet.
All it takes is creating a virtual private gateway, which is then linked to a specific VPC, and your information stays secure at all times on a private cloud connection of your very own.
What makes IoT VPCs so secure is that they require certain authentication from devices. For instance, most cellular IoT projects that leverage VPCs can grant permissions to specific devices in their deployment so that only a select number of users can access the VPC, greatly minimizing risk.
Offload Device Credentials to the Cloud

If a hacker is trying to break into your computer, it’s a lot easier if the credentials are stored on the laptop itself. The same logic applies to IoT devices. By burdening your IoT device with credentials, not only do you jeopardize your entire operation but you also tax your device resources, resulting in unnecessary data and power consumption.
One shortcut that businesses are using is offloading the encryption and authentication that devices need to access servers to the cloud itself. That way, your devices can stay lean and resource-efficient while the cloud — which has more than enough bandwidth for the job — handles the security.
Best of all, this is incredibly easy to set up. Your IoT devices send information using HTTP to a cloud adapter service which then transmits the data to the cloud into secure HTTPS. This trick is particularly useful for IoT projects that are deploying very low power and data devices such as IoT sensors that are infrequently sending small amounts of data.
And since the credentials are stored on the cloud-side, they can be remotely accessed on the fly, perfect for IoT projects that are expanding at full scale.
Real-Time Data Visualization
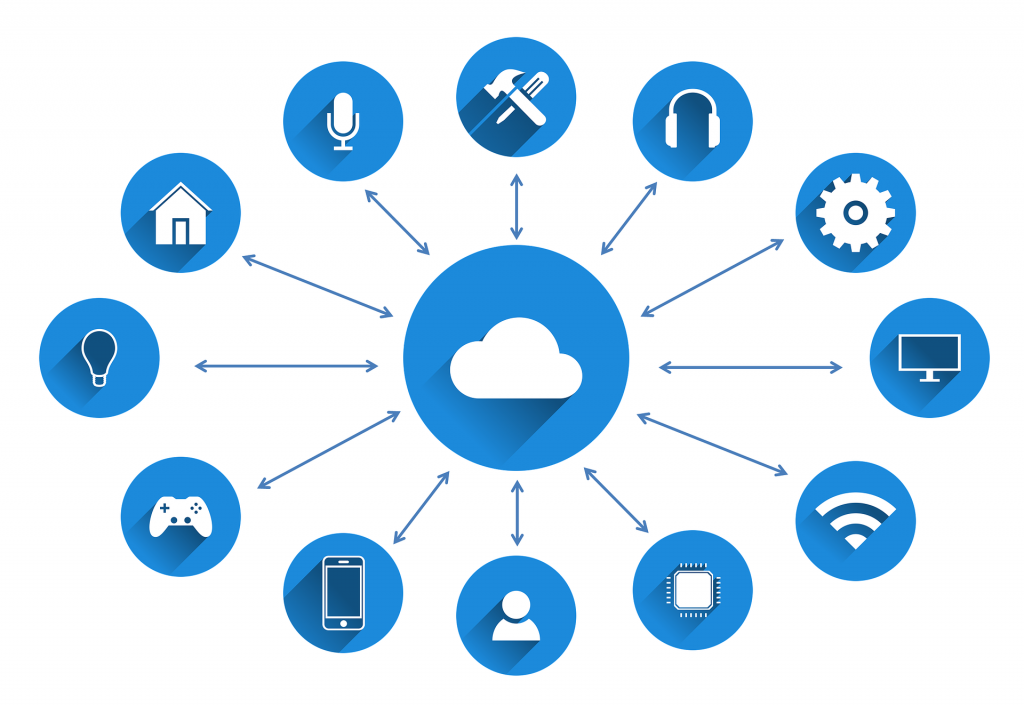
It’s far easier to notice a hijacked device when you can visualize its activity from your chair.
While data visualization provides tons of different benefits — ranging from business intelligence and marketing insights to performance visibility and sales analytics — it can also be a great way to spot rogue devices on your network.
Most of the time, these will be the ones that are sending unusual amounts of data, often to strange locations. Luckily, real-time data visualization can be quite simple for cellular IoT projects — without any need for a server or storage setup.
Once your devices are configured to send data to the software, you can start to visualize your data in a variety of different ways including GPS, time series and more. Plus, you can take these capabilities even further by building out an IoT dashboard complete with all of the specific parameters you want to watch for, such as time online, daily data volume, power consumption and more.With a watchful eye on your devices — regardless of the scale — it’ll be far easier to protect your IoT system from intruders.
The Ultimate IoT Security
With these improvements to your IoT security, you’re well on your way to creating a hack-proof project. However, for those that want to all but guarantee the safety and security of their data, it helps to team up with someone who knows a thing or two on the subject.
Soracom understands the importance of IoT security. Data transmission is a regular part of business for IoT projects but it does come with its risks.
Data breaches can not only affect your bottom line, but it can also directly impact the lives of your clients as well. That’s why we built a variety of different cloud-hosted software using the latest security features and protocols that minimize any risk involved in sending and receiving data.
Want to learn more ways to keep your data safe from potential hackers? Contact us today and let one of our team members help you lock down your IoT project.